Mitigating risks and implementing measures
Kubernetes offers comprehensive capabilities to secure clusters and operations. Although many security settings are suitable for rapid deployments, Cloud Native approaches provide a deep defense ("Defense in Depth").
This Kubernetes Security Library extends these approaches through various security levels:
An insecure container can be intercepted by a secure cluster, but not vice versa.
This library is action-oriented and distinguishes between Azure AKS and On-Premise environments.
top kubernetes risks
most important kubernetes security measures
The Kubernetes Security Library is based on the protection goal definition of the "Parkerian Hexad".
This deals with 6 basic protection goals:
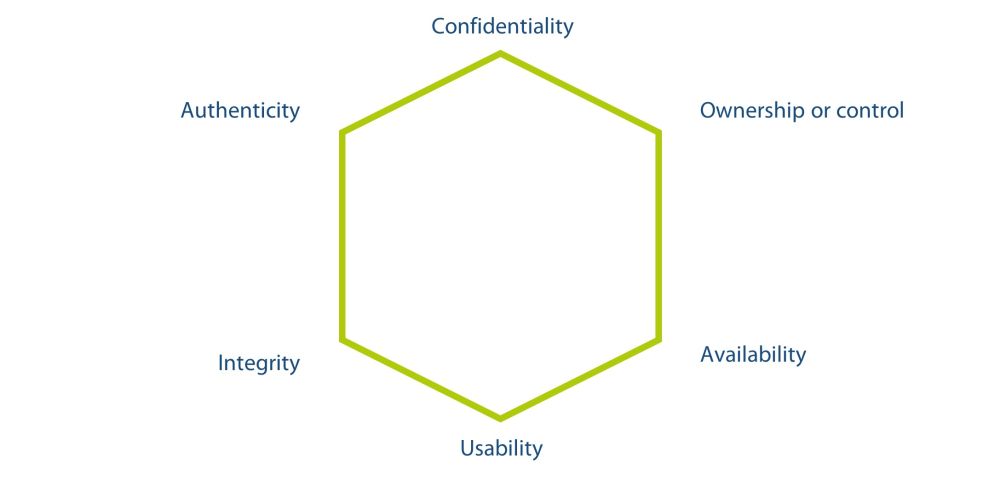
Confidentiality
Refers to the property that information is not made available to or passed on to unauthorized individuals.
Usability
Suppose a hacker encrypts one's data using, for example, ransomware. The affected data does not lose its confidentiality, integrity, or availability, but it is no longer usable.
Authenticity
Refers to the accuracy of the originating claim or authorship of the information. For example, one method of verifying the authorship of a handwritten document is to compare the handwriting characteristics of the document with a sample of others that have already been verified. For electronic information, a digital signature could be used to verify the authorship of a digital document using public key cryptography.
Ownership or control
A hacker steals encrypted data, even if the hacker cannot decrypt the data, the person who has been robbed is still concerned that the hacker could do so at any time now. This situation represents a loss of control or possession of information but does not involve a breach of confidentiality.
Availability
Means being able to access information in a timely manner. For example, both a hard disk crash and denial-of-service attacks result in an availability violation. Any delay that exceeds the expected service levels for a system can be called an availability violation.
Integrity
Refers to the accuracy or consistency with the intended state of information. Any unauthorized modification of data, whether intentional or accidental, is a violation of data integrity. For example, data stored on disk is expected to be stable - it should not be accidentally altered by problems with a disk controller. Similarly, application programs should record information correctly and not introduce deviations from intended values.
