Kubernetes Security library
Comprehensive security management and risk-minimizing measures for Kubernetes clusters.
Why the Kubernetes Security Library?
50+ security risks
Gain deep insights into over 50 critical security risks and how to manage them.


Over 100 measures
Find specific recommendations for action to effectively minimise risk.
Specific for Kubernetes
Customised security solutions for your Kubernetes infrastructure.


Continuous updates
Stay up to date with the latest safety research and regulation.
Practical expertise
Benefit from practical expertise for a robust security strategy.

Risks & Measures
An insecure container can be intercepted by a secure cluster, but not vice versa. This library is action-oriented and distinguishes between Azure AKS and On-Premise environments.
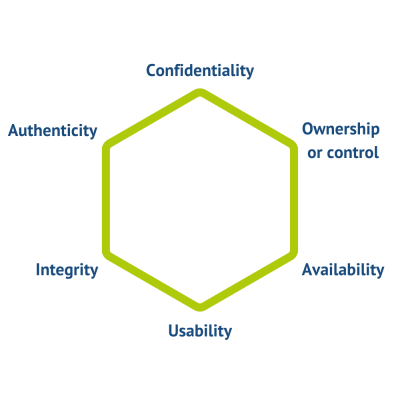
Parkerian Hexad
The Kubernetes Security Library is based on the protection goal definition of the "Parkerian Hexad".
This deals with 6 basic protection goals:
Refers to the property that information is not made available to or passed on to unauthorized individuals.
Means being able to access information in a timely manner. For example, both a hard disk crash and denial-of-service attacks result in an availability violation. Any delay that exceeds the expected service levels for a system can be called an availability violation.
Suppose a hacker encrypts one's data using, for example, ransomware. The affected data does not lose its confidentiality, integrity, or availability, but it is no longer usable.
Refers to the accuracy or consistency with the intended state of information. Any unauthorized modification of data, whether intentional or accidental, is a violation of data integrity. For example, data stored on disk is expected to be stable - it should not be accidentally altered by problems with a disk controller. Similarly, application programs should record information correctly and not introduce deviations from intended values.
Refers to the accuracy of the originating claim or authorship of the information. For example, one method of verifying the authorship of a handwritten document is to compare the handwriting characteristics of the document with a sample of others that have already been verified. For electronic information, a digital signature could be used to verify the authorship of a digital document using public key cryptography.
Container hardening from KubeOps
Do you want even more security for your Kubernetes clusters? With our special 5-level hardening you have the possibility to protect your containers even better. Visit our container hardening page for more information.

