Use Keycloak
2 minute read
keycloak
Now KubeOps-platform introduces keycloak, an one authentication and login system to use all the dashboards without the need of entering your credentials.
Install keycloak
you need kubeopsctl for installing keycloak: you need the parameter keycloak set to true:
...
keycloak: false # mandatory
...
later, you have configuration parameters for keycloak:
...
keycloakValues:
namespace: "kubeops" # Optional, default is "keycloak"
storageClass: "rook-cephfs" # Optional, default is "rook-cephfs"
keycloak:
auth:
adminUser: admin # Optional, default is admin
adminPassword: admin # Optional, default is admin
existingSecret: "" # Optional, default is ""
postgresql:
auth:
postgresPassword: "" # Optional, default is ""
username: bn_keycloak # Optional, default is "bn_keycloak"
password: "" # Optional, default is ""
database: bitnami_keycloak # Optional, default is "bitnami_keycloak"
existingSecret: "" # Optional, default is ""
...
Configure Dashboards for Keycloak
For Harbor
- Log in to the Harbor web console.
- Navigate to Administration > Configuration > Auth.
- Select OIDC as the Auth mode.
- Enter the required information from Keycloak:
-
OIDC Provider Name: Keycloak
-
OIDC Endpoint: (your Keycloak server URL)
-
OIDC Client ID: (The client ID you created in Keycloak for Harbor)
-
OIDC Client Secret: (The client secret you created in Keycloak for Harbor)
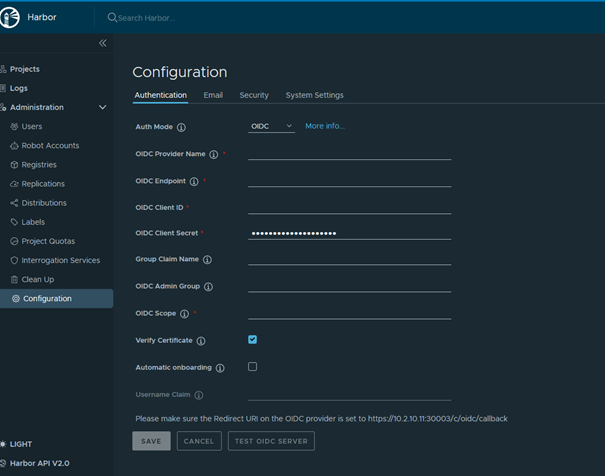
- Confirm the settings and test the login via Keycloak.
For Prometheus
- Keycloak supports OAuth2, which can be used for authentication with Prometheus. To do this, you must change the configuration of Prometheus to use the OAuth2 flow.
- in the prometheus.yml configuration file, you can add the authentication parameters under the oauth2 key:
scrape_configs:
- job_name: 'example-job'
oauth2:
client_id: 'your-client-id'
client_secret: 'your-client-secret
token_url: 'http://keycloak.example.com/auth/realms/your-realm/protocol/openid-connect/token'
For OpenSearch
- install the OpenSearch Security Plugin if it is not already installed.
- modify the OpenSearch security configuration file (config.yml) to use OIDC (OpenID Connect) for authentication:
authc:
openid_auth_domain:
http_enabled: true
transport_enabled: true
order: 0
http_authenticator:
type: openid
challenge: false
config:
subject_key: preferred_username
roles_key: roles
openid_connect_url: http://keycloak.example.com/auth/realms/your-realm/.well-known/openid-configuration