Blogs
Use of trusted registries for enhanced Kubernetes image security

Introduction
In the Kubernetes ecosystem, the security of container images is paramount. Trusted registries play a vital role in ensuring that only secure and verified images are deployed in Kubernetes clusters. This blog post explores the significance of trusted registries in Kubernetes image security and how to effectively implement them.
The Importance of Image Security in Kubernetes
Container images are the building blocks of Kubernetes deployments. Ensuring their security is not just a best practice but a necessity for several reasons:
Guarding Against Vulnerabilities: Container images can contain vulnerabilities, either in the application code or the underlying layers. Unchecked vulnerabilities can become gateways for attackers, leading to potential breaches and system compromises. Regular scanning and updating of container images are crucial in mitigating this risk.
Ensuring Regulatory Compliance: Many industries operate under strict regulatory requirements regarding data security and privacy. Using secure and compliant container images ensures that Kubernetes deployments adhere to these regulations, avoiding potential legal and financial repercussions.
Protecting Sensitive Data: Containers often handle sensitive data. Secure container images ensure that this data is processed and stored in an environment that is not exposed to risks like unauthorized access or data leaks.
Maintaining System Integrity: Secure container images contribute to the overall integrity of the Kubernetes system. They ensure that the deployed applications run as intended without being tampered with or modified by malicious entities.
Building Trust with End Users: In an era where data breaches are increasingly common, securing container images helps in building trust with end-users. It assures them that their data is handled in a secure, reliable environment.
Trusted Registries: The First Line of Defense
Trusted registries are integral to maintaining the security and integrity of container images in Kubernetes environments. They function as a controlled repository where images are stored, scanned, and managed with strict security protocols.
Automated Vulnerability Scanning: Trusted registries integrate tools for automated scanning of container images to detect vulnerabilities, malware, and misconfigurations. This continuous monitoring ensures that any security threats are identified and addressed promptly.
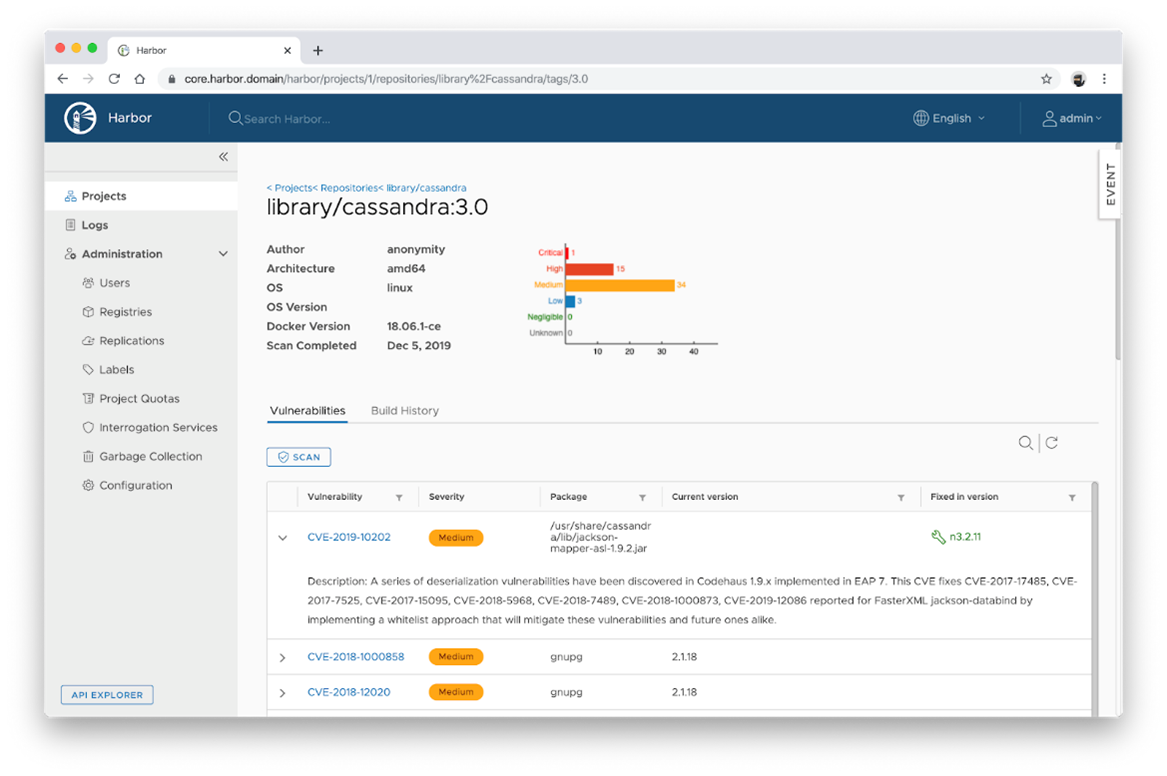
Quelle: https://goharbor.io/blog/img/interrogation-services.png
Image Signing and Verification: Implementing a process where images are digitally signed and verified before deployment ensures that only authenticated and untampered images are used in the Kubernetes environment. This process helps in maintaining the integrity of the images throughout their lifecycle.
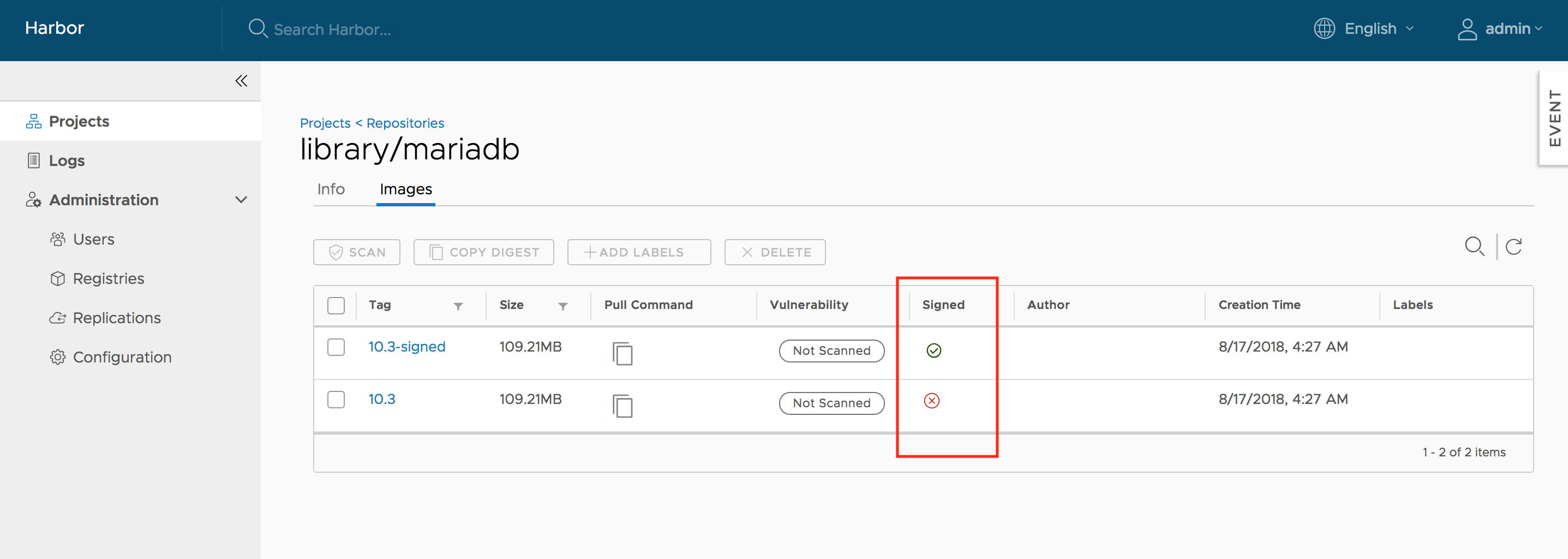
Quelle: https://goharbor.io/docs/2.7.0/img/content-trust.png
Robust Access Control: By enforcing strict access controls, trusted registries control who can upload (push) and download (pull) images. This ensures that only authorized personnel can modify or access the container images, reducing the risk of unauthorized manipulation or breaches.
Audit Trails and Compliance Reporting: Trusted registries keep a comprehensive log of all activities, including image uploads, downloads, and scanning results. These audit trails are crucial for compliance reporting and for tracing any security incidents back to their source.
Lifecycle Management of Images: These registries often include features for managing the lifecycle of container images, such as automated garbage collection, image versioning, and retention policies. This ensures that only relevant, up-to-date, and compliant images are available for deployment.
Implementing Trusted Registries in Kubernetes
Steps for implementation:
Selecting a Registry Provider: Choose a provider of private registries, like Harbor (included with KubeOps PLATFORM).

Configuring Image Pull Secrets: Set up secrets in Kubernetes for secure image pulling from private registries.
Automating Image Scanning: Integrate automated scanning tools like Trivy or Clair for continuous vulnerability assessment.
Best Practices for Using Trusted Registries
Using trusted registries effectively in Kubernetes is crucial for the security and integrity of containerized applications. Here are detailed best practices for leveraging trusted registries:
Regularly Update and Patch Registry Software: Ensure that the registry software is always up-to-date with the latest security patches and updates. Regularly updating the registry software helps protect against known vulnerabilities and security threats.
Enforce Strong Authentication and Authorization: Implement robust authentication mechanisms for users accessing the registry. Use role-based access control (RBAC) to define and enforce strict user permissions for different roles, ensuring that users can only perform actions that are necessary for their role.
Integrate with Continuous Integration/Continuous Deployment (CI/CD) Pipelines: Seamlessly integrate the trusted registry with CI/CD pipelines. This integration allows for the automated and secure transfer of images from the development stage to the registry and then to production environments.
Scan Images for Vulnerabilities Continuously: Utilize automated tools within the registry to continuously scan images for known vulnerabilities, malware, or misconfigurations. Regular scanning ensures that any risks are identified and remediated before the images are deployed.
Implement Immutable Tags: Use immutable tags for your container images to prevent overwriting. Once an image is tagged and pushed to the registry, the tag should not be reused. This practice helps in maintaining a clear and reliable history of image versions.
Monitor and Audit Registry Activity: Keep a close eye on the activities within the registry. Monitoring and auditing access and changes to the registry can help in early detection of any suspicious activities or security breaches.
Regular Backups: Regularly backup the registry data to prevent data loss in the event of a failure or breach. Ensure that these backups are stored securely and are easily recoverable.
Implement a Registry Quota Management System: Set quotas on the amount of storage each project or user can consume in the registry. This helps in managing resources efficiently and preventing misuse of the registry space.
Integrating Trusted Registries with Kubernetes
Integrating trusted registries within a Kubernetes environment is a crucial step in ensuring the security and reliability of containerized applications. Here's a detailed look into how this integration can be effectively achieved:
Use Kubernetes Secrets for Registry Authentication: Store the credentials for accessing the trusted registry securely in Kubernetes Secrets. This method ensures that sensitive data like usernames and passwords are stored in an encrypted format and are only accessible to authorized Kubernetes components.
Configure ImagePullSecrets for Pods: To ensure that Kubernetes pods can securely pull images from the trusted registry, configure ImagePullSecrets in the pod definitions. This Kubernetes object contains the necessary credentials to authenticate with the registry.
Set up Service Accounts with Proper Roles: Create and configure service accounts in Kubernetes with appropriate roles and permissions. These accounts should have the necessary permissions to pull images from the trusted registry and to execute other required tasks.
Automate Image Updates Using Webhooks: Implement webhooks in the registry to notify Kubernetes of new image versions. This automation can trigger a pipeline in Kubernetes to roll out updates to the applications smoothly and efficiently.
Implement Network Policies for Secure Communication: Establish Kubernetes network policies that define how pods can communicate with the trusted registry. This step ensures that only authorized services within the Kubernetes cluster can access the registry, enhancing security.
Leverage Kubernetes-native Tools for Registry Integration: Utilize Kubernetes-native tools and extensions like Helm charts or Operators that can simplify the process of integrating and managing the registry within the Kubernetes environment.
Monitor Registry Access and Activities: Continuously monitor the registry's access logs and activities from within Kubernetes. This practice helps in identifying any unusual access patterns or potential security threats.
Create a Redundant Setup for High Availability: To ensure high availability, configure a redundant setup for the trusted registry that Kubernetes can access. This setup could include replication of the registry across multiple nodes or cloud regions.
Conclusion
Securing container images with trusted registries is essential in Kubernetes environments. By implementing proper tools, practices, and integrations, organizations can significantly enhance the security and compliance of their Kubernetes deployments.

