Blogs
Securing Kubernetes Clusters with Advanced RBAC Strategies

Introduction
Kubernetes Role-Based Access Control (RBAC) is an essential component for securing Kubernetes clusters. It allows administrators to regulate access to Kubernetes API resources based on the roles of individual users within their organization. In this comprehensive guide, we will delve into the fundamentals of RBAC, how it functions in Kubernetes, and best practices for its implementation.
Understanding Kubernetes RBAC
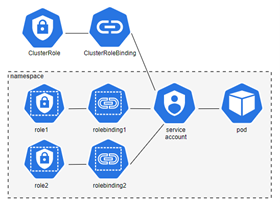
RBAC Principles in Kubernetes: Kubernetes RBAC operates on four main objects: Roles, ClusterRoles, RoleBindings, and ClusterRoleBindings. Roles and ClusterRoles define a set of permissions, while RoleBindings and ClusterRoleBindings grant those permissions to users, groups, or service accounts.
Roles vs ClusterRoles: A Role is a set of permissions that apply within a specific namespace. ClusterRoles, on the other hand, are cluster-wide and can be used to grant access across all namespaces.
RoleBindings and ClusterRoleBindings: RoleBindings grant the permissions defined in a Role to users within a specific namespace. ClusterRoleBindings grant the permissions defined in a ClusterRole across the entire cluster.
Understanding API Groups and Resources: In RBAC, permissions are granted for operations on specific API groups and resources. For example, you can grant a user permissions to read Pods within the “core” API group.
Default Roles and Bindings: Kubernetes comes with some default ClusterRoles such as cluster-admin, edit, and view, which offer different levels of access and can be bound to users, groups, or service accounts as needed.
Defining Roles and ClusterRoles: Step-by-Step Guide
Start by identifying the necessary permissions for different user groups within your organization. For instance, developers might need access to create and manage Pods, while operations teams might require broader cluster-level access.
Implementing RBAC in Kubernetes
Create YAML files for Roles and ClusterRoles. A Role might include permissions to read and write Pods and Services within a specific namespace, while a ClusterRole could include permissions to manage nodes and storage across the entire cluster.
Specify the API groups, resources, and verbs (such as get, watch, list, create, update, delete) in these YAML files. For example, a Role for pod management would look something like this:
yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: pod-manager
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch", "create", "update", "delete"]
Creating RoleBindings and ClusterRoleBindings: Assigning Roles to Users
After defining the Roles and ClusterRoles, you need to create RoleBindings or ClusterRoleBindings to assign these roles to actual users, groups, or service accounts.
A RoleBinding grants the permissions defined in a Role to a user or set of users within a specific namespace. For instance, binding the pod-manager role to a user in the default namespace would be defined as follows:
yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: pod-manager-binding
namespace: default
subjects:
- kind: User
name: alice
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: pod-manager
apiGroup: rbac.authorization.k8s.io
ClusterRoleBindings work similarly but are not restricted to a single namespace. They're ideal for assigning cluster-wide permissions, such as giving a group of users the ability to read secrets across all namespaces.
Best Practices in Kubernetes RBAC
Using Namespaces for Structured Access Control
Utilize Kubernetes namespaces to create isolated environments within the cluster. This can be useful for separating development, staging, and production environments or different teams.
Assign RoleBindings within these namespaces to control who has access to what within each isolated environment. This is crucial for maintaining security and order, especially in large-scale deployments.
Managing Users and Groups Outside Kubernetes
Remember, Kubernetes itself does not manage the creation or management of users. Instead, user management is typically handled outside Kubernetes, such as through your organization’s identity provider.
Use group memberships managed in your identity provider to map users to roles in Kubernetes, providing a scalable way to manage access.
Leveraging Service Accounts for Automated Access
For processes that require automated access to the Kubernetes API, such as continuous integration and deployment pipelines, create and use service accounts.
These service accounts can be bound to specific roles within the cluster, ensuring that automated processes have the necessary permissions to function correctly without manual intervention.
Principle of Least Privilege
Always assign the minimum permissions necessary for a user or service to perform its intended function. This reduces the risk of unauthorized access or damage in case of a compromised account.
Regularly review and update RBAC settings to ensure they align with current roles and responsibilities within your organization.
Regular Audits and Revisions
Conduct periodic audits of RBAC policies to identify and rectify any redundant, outdated, or overly permissive access rights.
Implement a process for reviewing RBAC policies whenever there are changes in team structures, projects, or Kubernetes updates.
Use Namespaces Wisely
Structure your Kubernetes cluster with namespaces to segregate resources by teams, projects, or environments. This simplifies RBAC management by limiting the scope of roles and permissions.
Assign RoleBindings within namespaces for fine-grained access control and to prevent accidental access or changes to resources in other namespaces.
Manage Service Account Permissions
Be cautious with the permissions granted to service accounts as they are often used by applications and automation tools. Restrict their access to only what's necessary for their specific function.
Avoid using default service accounts for workload pods, as they may inherit broad cluster-level permissions. Instead, create dedicated service accounts with precise role bindings.
Integrate with External Identity Providers
If possible, integrate Kubernetes RBAC with external identity providers. This allows you to manage user access centrally and leverage existing organizational structures and access policies.
Utilize group-based access control by mapping groups from your identity provider to roles in Kubernetes, streamlining the management process.
Documentation and Policy as Code
Document your RBAC policies, including the rationale behind each role and binding. This is crucial for maintaining clarity and simplifying future audits.
Treat RBAC configurations as code – version control your RBAC definitions to keep track of changes and facilitate rollbacks if needed.
Automated RBAC Configuration and Enforcement
Use automation tools for configuring and enforcing RBAC policies to minimize human errors and efficiently handle complex configurations.
Consider tools that provide visualization of RBAC settings, making it easier to understand and manage complex access structures.
Training and Awareness
Ensure your team understands the importance of RBAC in maintaining cluster security. Provide training on best practices and common pitfalls.
Encourage a security-conscious culture where team members feel responsible for the access rights they hold and understand the implications of their actions within the Kubernetes environment.
Test RBAC Settings
Regularly test RBAC configurations to ensure they work as intended. This can be done through role-playing scenarios or automated testing tools.
Include RBAC configurations in your disaster recovery plans. Ensure you have a process for quickly restoring access rights in case of an incident.
Monitor and Alert
Implement monitoring for RBAC-related changes and activities. Set up alerts for unusual access patterns or modifications to critical roles and bindings.
By adhering to these best practices, organizations can effectively leverage Kubernetes RBAC to enhance security, streamline access management, and maintain a robust and scalable container orchestration environment.
Advanced RBAC Strategies
Conditional Access Based on Context: Implement conditional access policies that take into account the context of the request, such as the source IP.
Integrating with External Identity Providers: Leverage integration with external identity providers for managing user identities and group memberships.
Automating RBAC with Operators: Utilize Kubernetes Operators to automate the management and enforcement of RBAC policies.
Handling Cross-cluster RBAC: In multi-cluster environments, consider strategies for consistently applying RBAC policies across clusters.
RBAC for Specialized Kubernetes Resources: Understand and apply RBAC for specialized resources like Custom Resource Definitions (CRDs) or namespaces with specific requirements.
Conclusion
Effective RBAC implementation in Kubernetes is crucial for maintaining robust security and operational efficiency. By understanding the core concepts, following best practices, and leveraging advanced strategies, organizations can achieve a secure and well-managed Kubernetes environment.

