Blogs
Audit Logs in Kubernetes: Ensuring Security and Compliance

Introduction
Kubernetes, as a container orchestration platform, is not just about managing applications but also ensuring their security. One critical aspect of Kubernetes security is monitoring audit logs. These logs provide a chronological record of events that have occurred in the Kubernetes cluster, offering insights into security-related incidents and operational activities.
Understanding Kubernetes Audit Logs


Kubernetes audit logs are comprehensive records of events and interactions within a Kubernetes cluster. These logs are pivotal for several reasons:
Tracking API Interactions: Every request made to the Kubernetes API is logged, detailing who initiated the request, what was requested, and the response from the server. This is crucial for understanding how users and applications are interacting with the cluster.
Security Surveillance: Audit logs are instrumental in identifying security incidents. By analyzing these logs, administrators can detect abnormal patterns that may indicate a security threat, such as unauthorized access attempts or unexpected changes in resource deployment.
Compliance and Auditing: Many industries require strict compliance with security standards. Audit logs serve as a record for compliance purposes, proving that the cluster adheres to the necessary regulations.
Operational Troubleshooting: Audit logs can be used to troubleshoot operational issues within the cluster. They provide a chronological account of events leading up to an issue, aiding in pinpointing the cause.
Forensic Analysis: In the event of a security breach, audit logs are invaluable for forensic analysis. They provide a detailed timeline of events, helping to identify how the breach occurred and the extent of its impact.
User and Application Behavior Analysis: By examining audit logs, administrators can understand how users and applications typically interact with the cluster, which is useful for optimizing performance and user experience.
Resource Utilization Tracking: Audit logs can show trends in resource usage, helping administrators make informed decisions about scaling and resource allocation.
Detecting Configuration Changes: Any changes in cluster configuration are recorded in audit logs. This helps in tracking modifications that could affect cluster performance or security.
Configuring Audit Logs in Kubernetes: To effectively utilize audit logs, they must be correctly configured. This involves setting up audit policies and backends.
Audit Policy: Defines what actions should be logged and at what level of detail. This includes decisions on logging metadata, request bodies, and responses for different API groups and resources.
Audit Backend: Determines where the audit logs are sent. Kubernetes supports two types of backends:
- Log Backend: Writes audit logs to a file on the master node.
- Webhook Backend: Sends audit logs to an external HTTP(S) service.
Analyzing Audit Logs for Security

Audit logs are a goldmine for security analysis. Key areas to focus on include:
Identifying Unauthorized Access Attempts: Logs showing failed access attempts can indicate security breaches.
Monitoring for Unusual Resource Access Patterns: Repeated or unexpected access to sensitive resources could signal a threat.
Tracking Changes in Roles and Permissions: Monitoring sudden role and permission changes for potential security risks.
Analyzing User Behavior Anomalies: Unusual behavior patterns in user actions, such as atypical access times or frequency, can hint at compromised accounts.
Scrutinizing Network Access Patterns: Logs showing abnormal network access patterns, like spikes in traffic from unknown IPs, could indicate external threats.
Detecting Data Exfiltration Attempts: Monitoring for unusual data retrieval or transfer activities that may suggest data theft.
Correlating Events Across Logs: Cross-referencing events across various logs to uncover coordinated attack patterns.
Alerting on Suspicious Activities: Implementing automated alerts for suspicious activities detected in audit logs.
Best Practices for Audit Log Management
For effective management:
Routine Log Monitoring: Regular review of logs for any unusual activities.
Integration with Analysis Tools: Utilizing tools like ELK Stack or Splunk for in-depth log analysis.
Archiving and Retention Policies: Ensuring logs are archived and retained for necessary periods for compliance and future analysis.
Log Analysis Training: Training staff in effectively reading and understanding audit logs for better security insights.
Automated Analysis and Reporting: Implementing automated tools for continuous log analysis and regular reporting.
Incident Response Planning: Having plans in place for responding to security incidents identified through audit logs.
Regular Audit Log Reviews and Audits: Conducting periodic reviews and audits of the audit logs to ensure they are capturing the necessary data effectively.
Secure Log Storage: Ensuring audit logs are stored securely to prevent unauthorized access or tampering.
Tools for Enhanced Audit Log Analysis
Several tools can enhance the analysis of Kubernetes audit logs:

Falco: Detects suspicious activities in real-time.
Example Architecture:
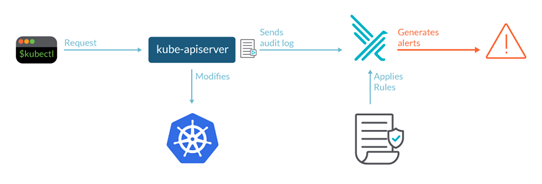

Fluentd: Aggregates and forwards logs to external systems.

Prometheus & Grafana: For visualizing log data and setting up alerts.
Conclusion
Audit logs are an indispensable tool for maintaining the security and integrity of Kubernetes clusters. Proper configuration, regular monitoring, and effective analysis of audit logs are vital for detecting and responding to security incidents, ensuring compliance, and optimizing cluster performance.

