Blogs
Automate TLS Certificate Management in Kubernetes with Cert-Manager

Introduction
As modern applications and services increasingly migrate to Kubernetes, managing various aspects such as security and configuration becomes more complex. One of the critical aspects of this management is handling TLS certificates.
In this comprehensive guide, we’ll delve into how you can effectively manage certificates in Kubernetes using Cert-Manager, a powerful, open-source tool designed to automate the management and issuance of TLS certificates.
What is Cert-Manager?
Cert-Manager is a Kubernetes native application that automates the management and issuance of TLS certificates. It simplifies the process of obtaining, renewing, and using those certificates.
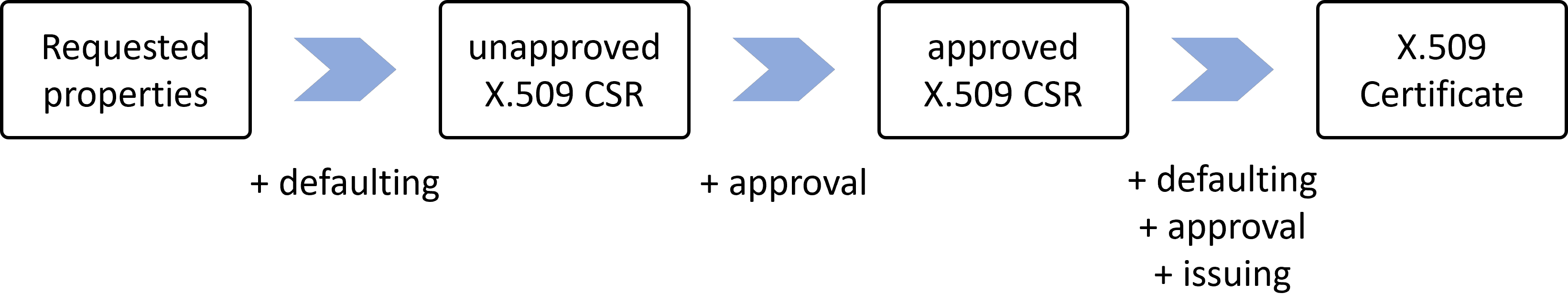
Quelle: https://cert-manager.io/images/high-level-overview.svg
Why Use Cert-Manager?
Automation of Certificate Issuance and Renewal: Cert-Manager automates the process of certificate issuance and renewal, reducing manual efforts and minimizing the risks of expired certificates.
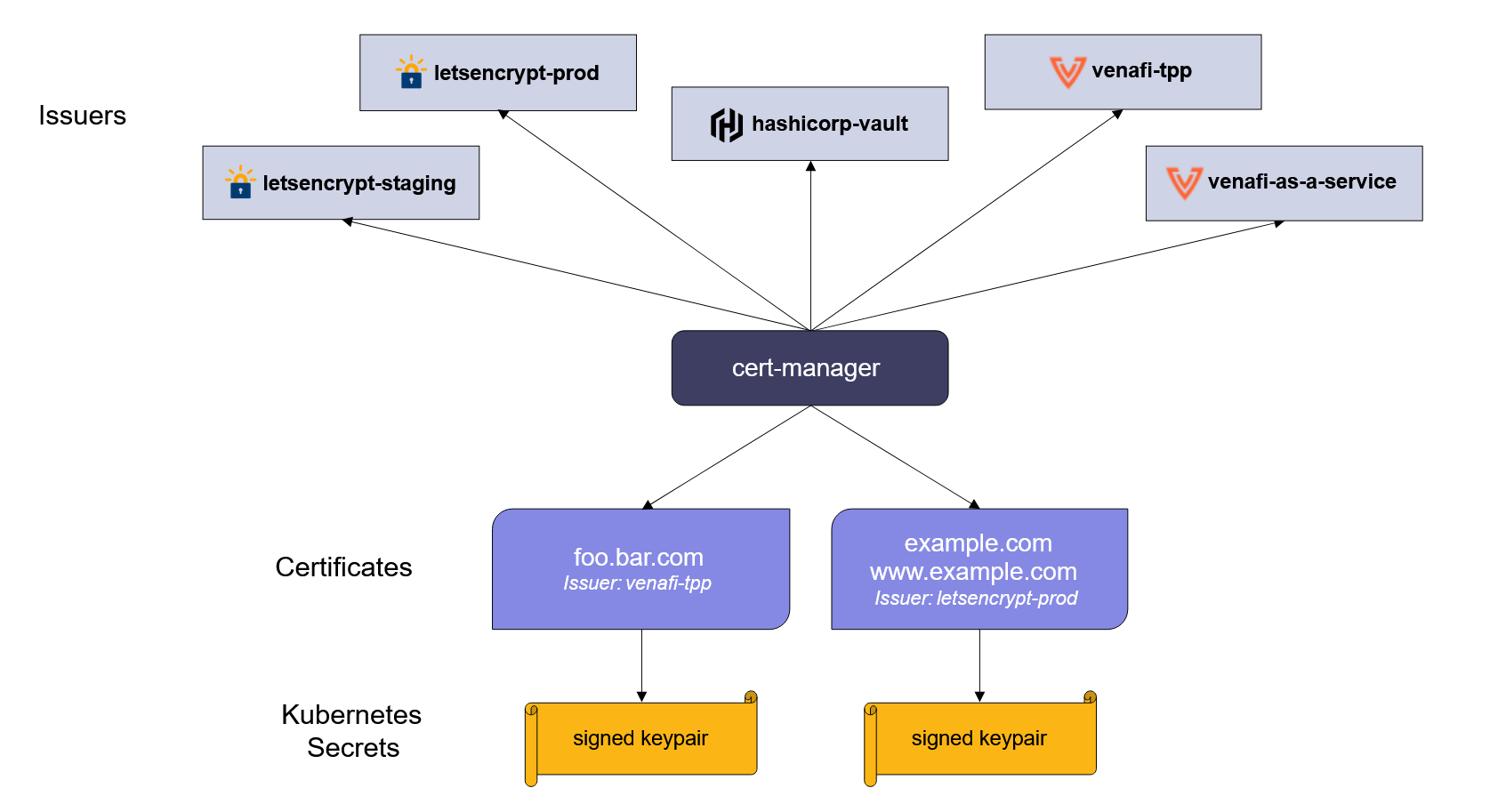
Integration with Multiple Issuers: It supports various certificate authorities like Let's Encrypt, HashiCorp Vault, and self-signed certificates, providing flexibility in certificate management.
Native Kubernetes Integration: Being Kubernetes-native, it integrates seamlessly with Kubernetes resources and paradigms.
Custom Resource Definitions (CRDs): Cert-Manager uses CRDs for managing certificates, making it easy to define and manage certificates as part of your Kubernetes manifests.
Quelle: https://cert-manager.io/images/issuance-flow-policy.png
Installing Cert-Manager
To install Cert-Manager in your Kubernetes cluster, you can use Helm charts or apply YAML manifests directly. Here’s a step-by-step guide:
Prerequisites: Ensure you have a running Kubernetes cluster and kubectl configured to communicate with your cluster.
Install with Helm (recommended):
Add the Jetstack Helm repository.
helm repo add jetstack https://charts.jetstack.io
Update your local Helm chart repository cache.
helm repo update
Install Cert-Manager with Helm.
helm install \
cert-manager jetstack/cert-manager \
--namespace cert-manager \
--create-namespace \
--version v1.13.2 \
--set installCRDs=true
Configuring Cert-Manager involves setting up issuers or cluster issuers and creating certificate resources.
Setting Up Issuers: Issuers are Kubernetes resources that represent certificate authorities. They can be scoped to a namespace (Issuer) or cluster-wide (ClusterIssuer).
Creating Certificate Resources: Define a Certificate resource in your Kubernetes manifest, specifying the desired certificate's details like common name, DNS names, and the issuer.
Using Cert-Manager with Ingress
Cert-Manager can be integrated with Kubernetes Ingress to secure your applications automatically. By annotating your Ingress resource, you can instruct Cert-Manager to issue and renew certificates for your application.
Annotate Your Ingress Resource: Add annotations to your Ingress resource to specify the issuer and enable automatic certificate management.
Verify Certificate Issuance: Once your Ingress resource is deployed, Cert-Manager will issue a certificate and ensure it is renewed before expiration.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: example-ingress
annotations:
cert-manager.io/cluster-issuer: "letsencrypt-prod"
kubernetes.io/ingress.class: "nginx"
spec:
tls:
- hosts:
- example.kubeops.net
secretName: example-tls
rules:
- host: example.kubeops.net
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: example-service
port:
number: 80
Best Practices and Tips
Regularly Back Up Cert-Manager Resources: Ensure you have backups of your Cert-Manager resources like certificates and issuers.
Monitor Cert-Manager: Set up monitoring and alerts for Cert-Manager to keep track of its health and the status of certificates.
Use a Staging Environment for Testing: Before issuing production certificates, test your configuration in a staging environment.
Conclusion
Cert-Manager significantly simplifies TLS certificate management in Kubernetes, automating the issuance and renewal processes.
By integrating Cert-Manager into your Kubernetes environment, you can ensure your applications are secure with valid TLS certificates, minimizing manual intervention and potential downtime due to expired certificates.