Blogs
Enhancing Container Security with Trivy: Identifying and Mitigating Vulnerabilities

The present-day digital landscape is increasingly moving towards containerized deployment. This mechanism involves the encapsulation of applications along with their dependencies into standalone units, termed containers. Such a method ensures consistency across different environments but also presents unique security challenges. As the container ecosystem evolves, tools like Trivy have emerged to address these challenges.
Here, we explore Trivy, a cutting-edge tool that specializes in identifying vulnerabilities within these containers.
1. Containers: A Deep Dive into Modern Deployment Techniques
What are Containers? Containers are akin to self-sufficient packages that house an application alongside all its necessary components, including libraries, binaries, and configurations. This encapsulation ensures a uniform behavior of the application irrespective of the environment.
At its core, a container is a standalone package. This means that everything required to make an application run is housed within the container itself – the code, runtime, system tools, system libraries, and settings.
Advantages of Using Containers: One of the significant boons of containerization is its ability to maintain consistent deployments. It greatly minimizes the disparity between development and production environments.
Potential Security Pitfalls: While containers offer deployment advantages, they can sometimes include vulnerabilities from base images or dependencies.
A Practical Example: Consider a service like Netflix, which has global operations and releases numerous updates. Containerization aids in achieving such frequent deployments.
2. The Role of Vulnerability Scanning in Container Security
Why Scan for Vulnerabilities? It's vital to recognize that containers could harbor vulnerabilities. If overlooked, these vulnerabilities can lead to various challenges, including data breaches and service disruptions.
Varieties of Vulnerabilities: Vulnerabilities can arise from multiple sources, such as OS packages, application code, or third-party libraries. A comprehensive scanning tool should be adept at identifying these diverse vulnerabilities.
Prior to Tools like Trivy: There were other vulnerability scanners, but many lacked specific features tailored for containers or were not as efficient in certain aspects.
3. Trivy vs Other Scanners:
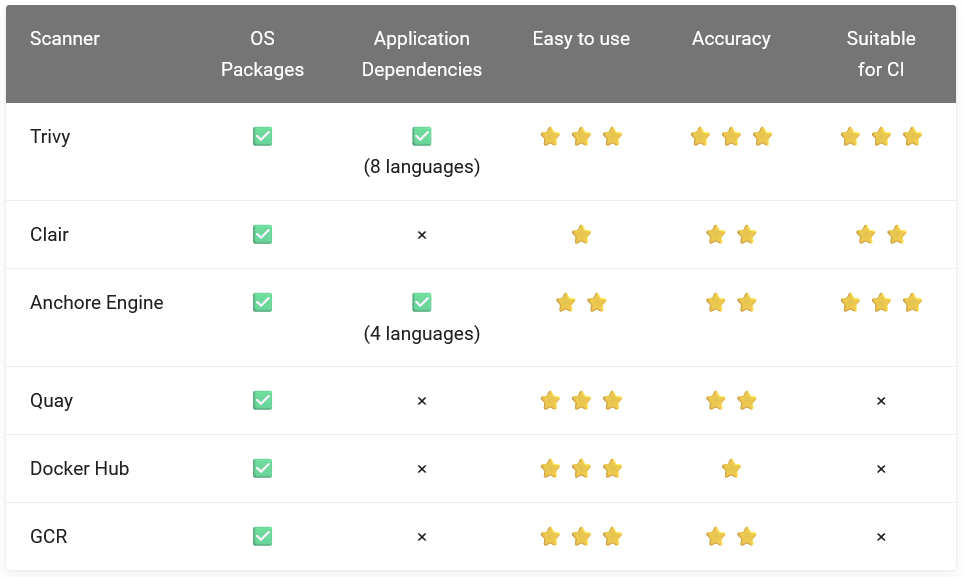
4. A Closer Look at Trivy: Its Role in Container Security
Developed by Aqua Security, Trivy is an open-source vulnerability scanner tailored for containers. It can scan both OS packages and application dependencies with ease.
Trivy is able to scan for private and public registries, local filesystems, and container formats such as tar archives, Podman and Git repositories. Achieve functionality for a variety of execution environments, such as Linux, macOS, FreeBSD, and OpenBSD, with the option to support air-gapped environments as well as distroless images.
How Does Trivy Operate?
Trivy employs a continually updated database, ensuring a comprehensive scan that recognizes even recently discovered vulnerabilities.
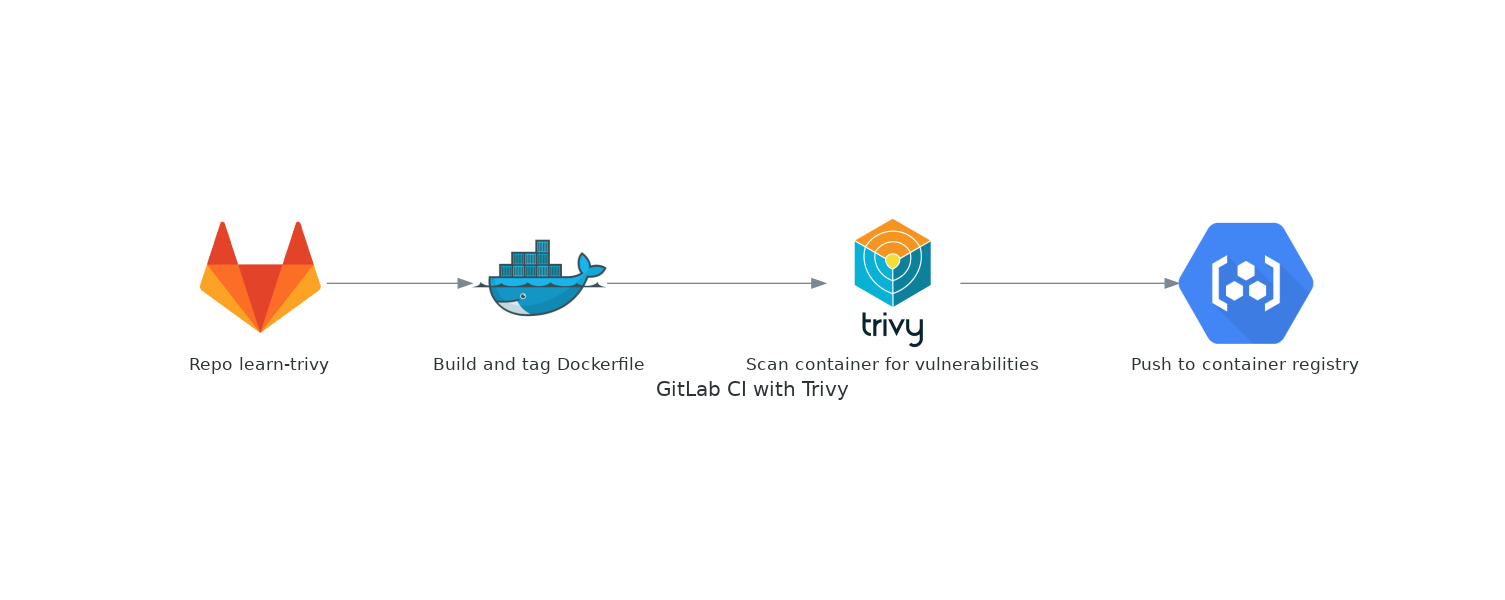 Compatibility and Support: Trivy is designed to be versatile, supporting various distributions ranging from Debian and Ubuntu to Alpine and many RPM-based systems.
Compatibility and Support: Trivy is designed to be versatile, supporting various distributions ranging from Debian and Ubuntu to Alpine and many RPM-based systems.
5. Observing Trivy in a Practical Setting
Setting Up Trivy: For those interested in using Trivy, the setup is relatively straightforward. The tool provides flexibility, allowing users to choose between different installation methods. Also you can easily enable on Harbor Private registry deployment.
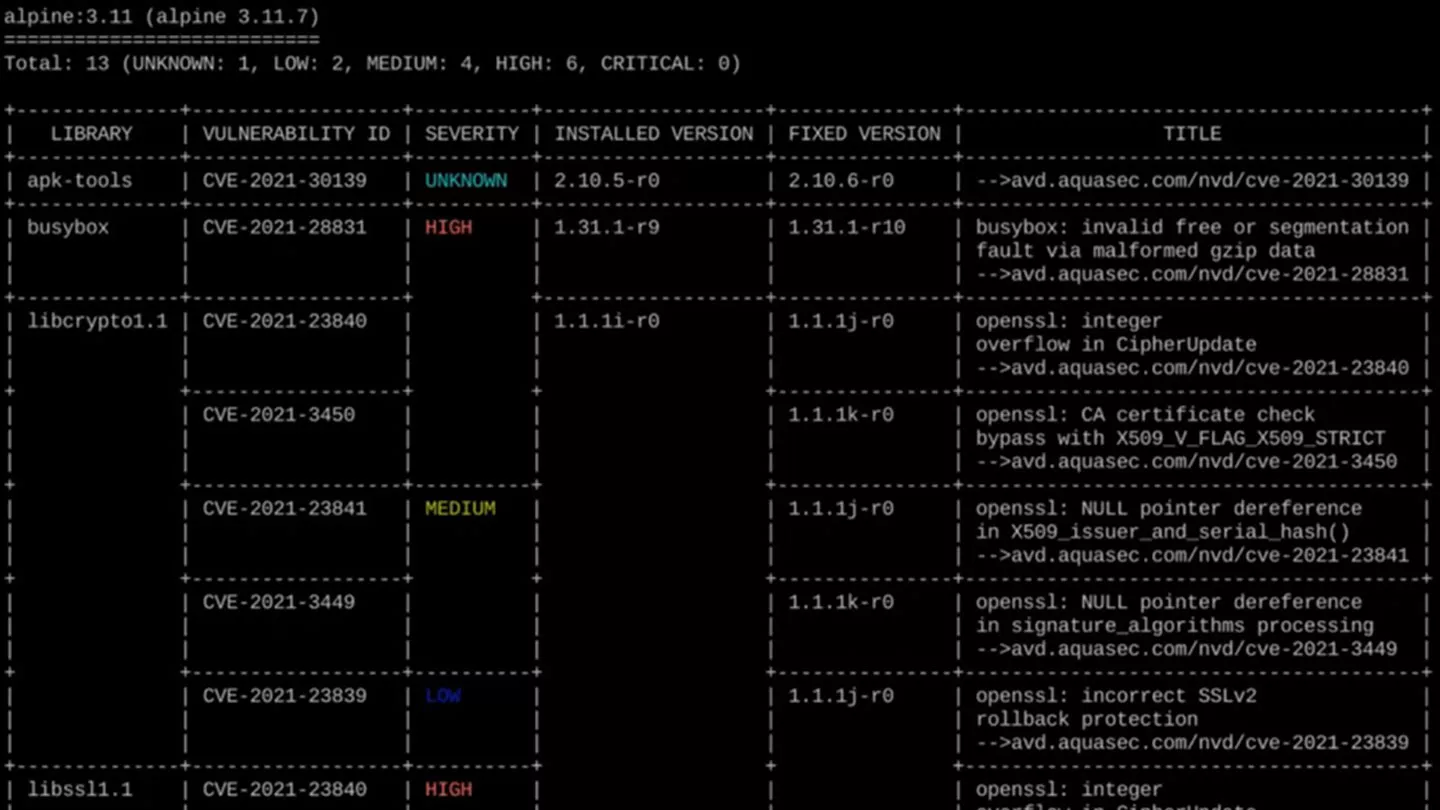
Sample Vulnerability Scan: When applied to a container, for instance, one that hosts a Node.js application, Trivy might identify vulnerabilities within specific npm packages, giving users insights into potential risks.
Decoding Trivy's Reports: Trivy provides detailed reports that categorize vulnerabilities based on their severity, aiding users in prioritizing their response.
6. Beyond Scanning Mitigation and Best Practices
Identifying vulnerabilities is just the first step. Ensuring they don't pose a threat is crucial:
Mitigating Vulnerabilities: Once identified, vulnerabilities should be addressed promptly. This might involve updating libraries, patching the OS, or rectifying the application code.
Regular Scanning: Just like regular health check-ups, containers should undergo frequent vulnerability scans to ensure they remain secure as they evolve.
Staying Updated: With the cyber threat landscape continually evolving, it's essential to stay informed. Subscribing to vulnerability databases or security news feeds can help in this endeavor.
Conclusion
In the vast world of container security, tools like Trivy act as guiding lights, ensuring that as we leverage the benefits of containerization, we don't compromise on security. While this introduction provides a comprehensive overview, we encourage those interested to delve deeper, exploring Trivy's extensive documentation and joining its vibrant community.

